查找方法
过于漏洞记录的网站国内外有很多,我只介绍下面两个:
利用cve list查询已经发布的漏洞:
https://cve.mitre.org/cgi-bin/cvekey.cgi?keyword=camera


利用exploit database查询,在我看来,exploit database的数据更将丰富清晰,但是漏洞库相比较少。
https://www.exploit-db.com/exploits
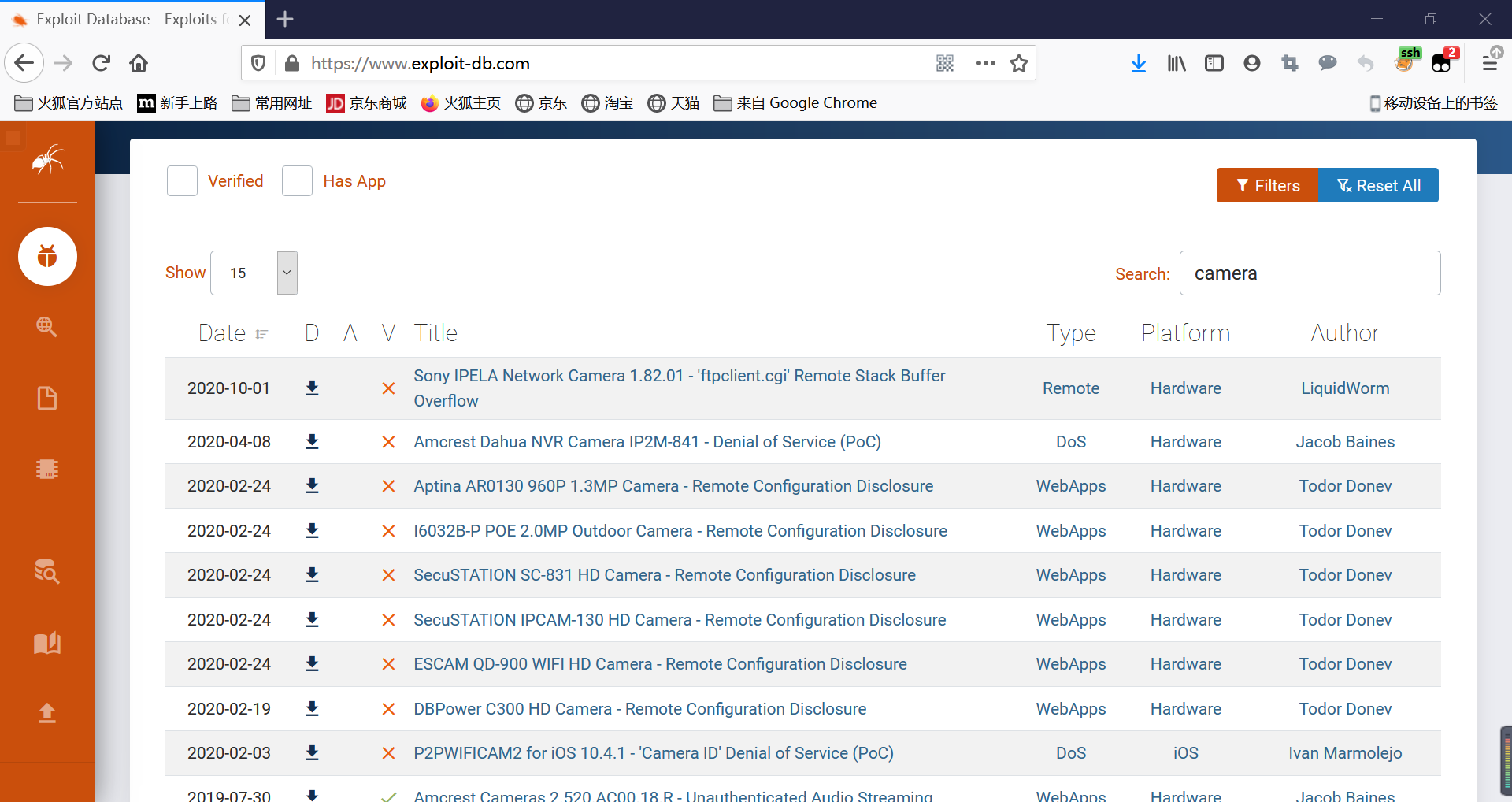
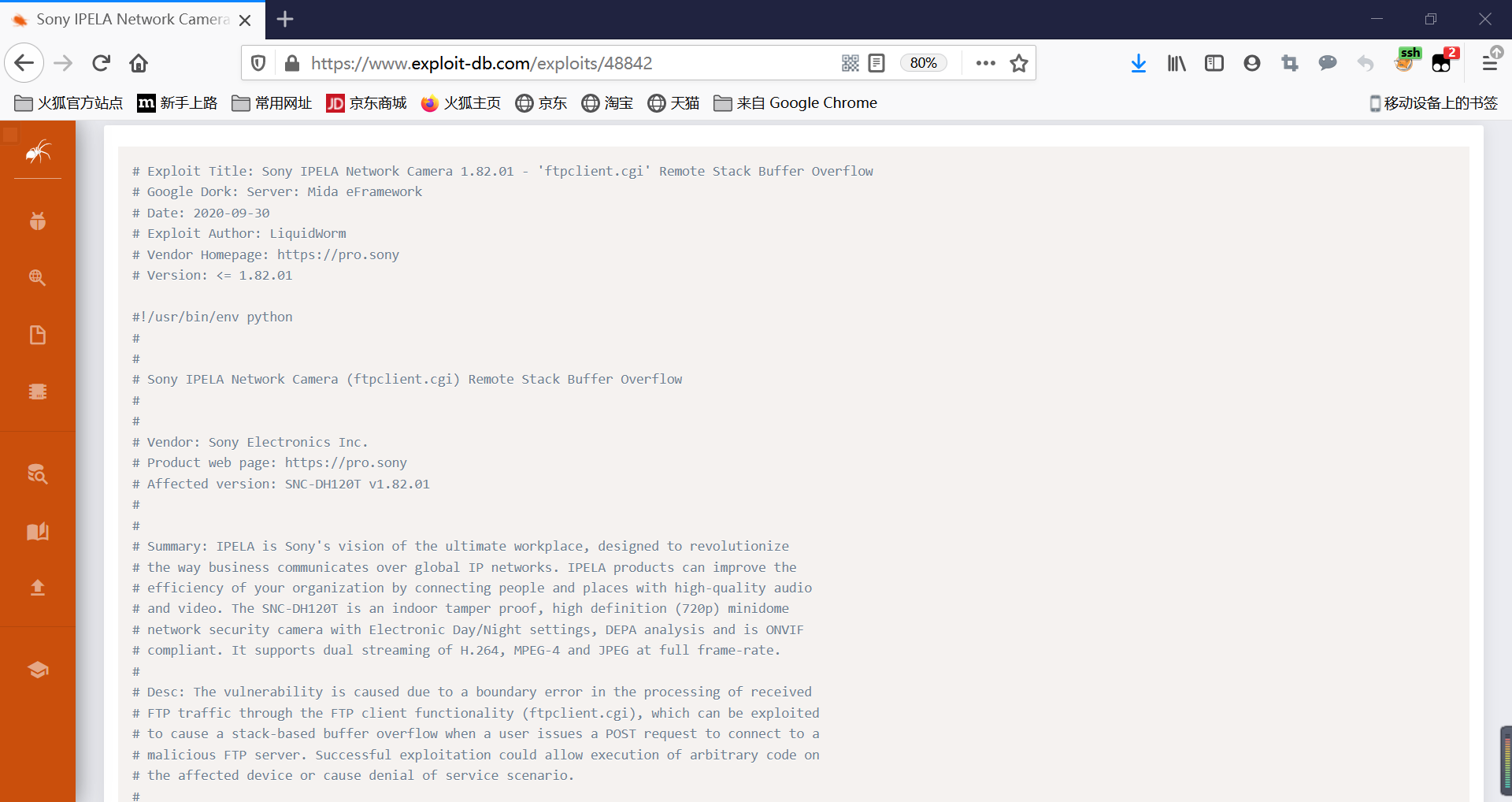
工欲善其事必先利其器
binwalk(解压固件包、查看固件信息) + ghidra(调试)
下载地址:https://pan.baidu.com/s/1IY5YiIXuEmsCvglt0qgrzw 提取码: 78tu
关于固件的下载和说明文档,我的建议是————百度
下面我来介绍一个例子:D-Link DIR-645路由器
漏洞描述:

固件下载地址:
链接: https://pan.baidu.com/s/1C1koxw1r6uOHzoNAo7PrmQ 提取码: mta9
漏洞分析:
__查询签名得到架构的信息__(一般是x86,x86_64,i386,amd64,mips,arm)
(啥都没有,没关系)
解压:
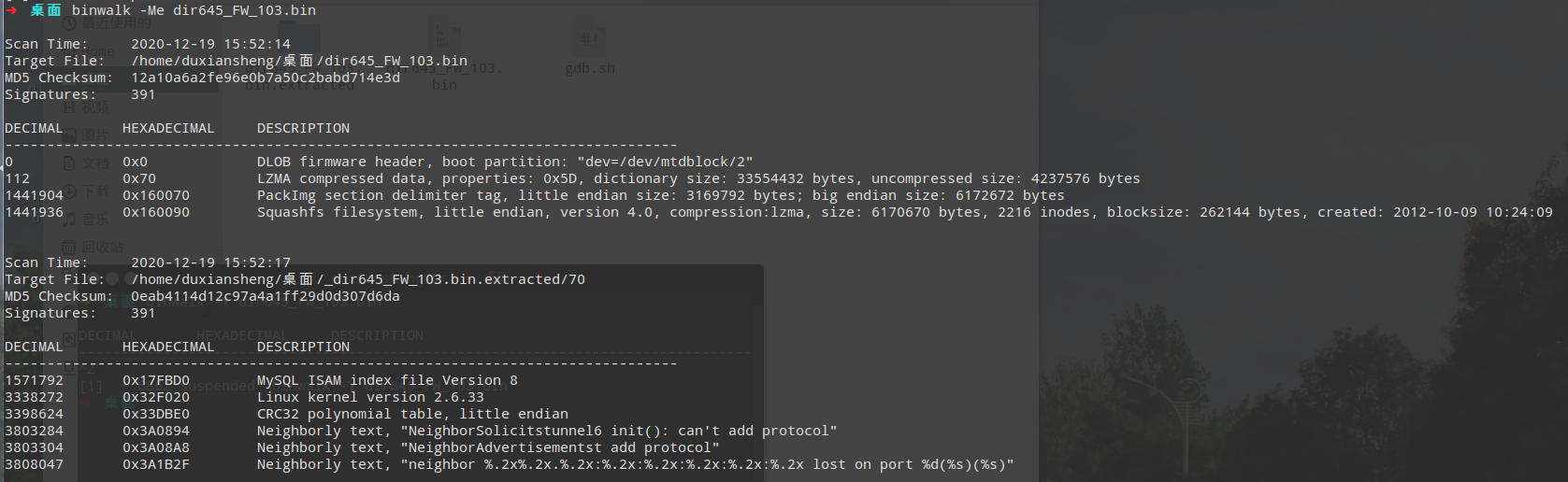
搜索busy文件查看系统构架:
busybox是嵌入式设备常用(基本上都要用)的工具,它里面集成了很多linux常用命令并且文件本身比较小。这里搜索到了这个文件说明解压成功了(也可以通过tree命令查看目录里面文件多少判断是否解压成功)

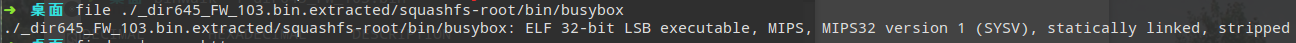
32位,mips架构
查看漏洞:
根据搜索到的文档,我们已经知道漏洞在文件authentication.cgi中,所以我们在解压的固件中直接查找此文件,这是一个公共网关接口,而真正的目标文件是cgibin
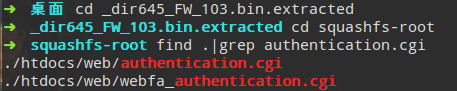
(ll不是linux下一个基本的命令,它实际上是ls -l的一个别名)

顺便提一下,有时候分析文章是没有给出是哪个文件
一般是httpd文件(如果是http服务的漏洞)
在找到文件后直接拖入ida7.5(可以打开mips架构文件)中,
寻找authenticatecgi_main函数:
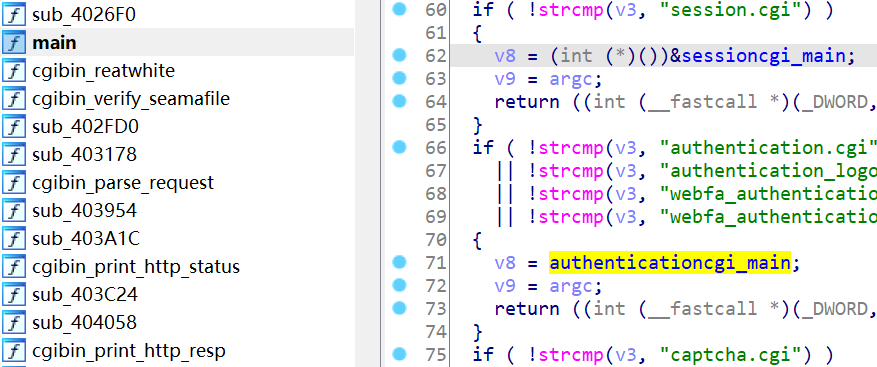
漏洞所在:read函数没有验证参数nbytes大小,将用户可控的输入内容放置大小固定的栈中局部变量,从而发生溢出!
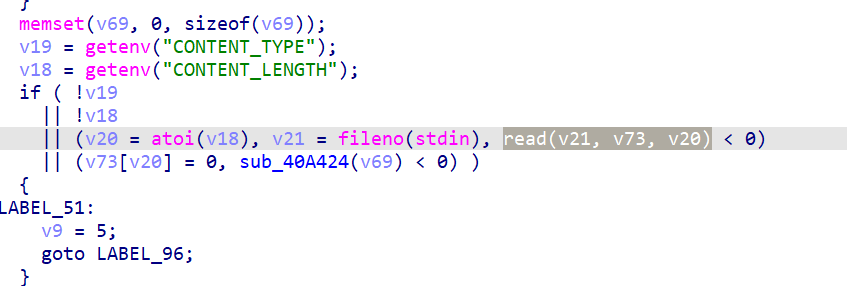
具体调试及复现可以参考:
https://bbs.pediy.com/thread-259274.htm
附:
ubuntu的apt及pip自动下载换源脚本
#!/bin/bash
sudo mv /etc/apt/sources.list /etc/apt/sources.list.bak.1
codename=`lsb_release -c | cut -c 11-`
echo "codename is $codename"
sudo touch /etc/apt/sources.list
sudo echo "deb http://mirrors.aliyun.com/ubuntu/ $codename main restricted universe multiverse" >> /etc/apt/sources.list
sudo echo "deb-src http://mirrors.aliyun.com/ubuntu/ $codename main restricted universe multiverse" >> /etc/apt/sources.list
sudo echo "deb http://mirrors.aliyun.com/ubuntu/ $codename-security main restricted universe multiverse" >> /etc/apt/sources.list
sudo echo "deb-src http://mirrors.aliyun.com/ubuntu/ $codename-security main restricted universe multiverse" >> /etc/apt/sources.list
sudo echo "deb http://mirrors.aliyun.com/ubuntu/ $codename-updates main restricted universe multiverse" >> /etc/apt/sources.list
sudo echo "deb-src http://mirrors.aliyun.com/ubuntu/ $codename-updates main restricted universe multiverse" >> /etc/apt/sources.list
sudo echo "deb http://mirrors.aliyun.com/ubuntu/ $codename-backports main restricted universe multiverse" >> /etc/apt/sources.list
sudo echo "deb-src http://mirrors.aliyun.com/ubuntu/ $codename-backports main restricted universe multiverse" >> /etc/apt/sources.list
sudo echo "deb http://mirrors.aliyun.com/ubuntu/ $codename-proposed main restricted universe multiverse" >> /etc/apt/sources.list
sudo echo "deb-src http://mirrors.aliyun.com/ubuntu/ $codename-proposed main restricted universe multiverse" >> /etc/apt/sources.list
sudo apt-get update
if [ ! -d ~/.pip ];then
mkdir ~/.pip
fi
if [ -f ~/.pip/pip.conf ];
then
sudo mv ~/.pip/pip.conf ~/.pip/pip.conf.bak
sudo touch ~/.pip/pip.conf
else
sudo touch ~/.pip/pip.conf
fi
sudo echo "[global]" >> ~/.pip/pip.conf
sudo echo "index-url = https://mirrors.aliyun.com/pypi/simple" >> ~/.pip/pip.conf
|
binwalk完整下载脚本:
#!/bin/bash
sudo apt -y install python-lzma python-crypto
sudo apt -y install libqt4-opengl python-opengl python-qt4 python-qt4-gl python-numpy python-scipy python-pip
sudo pip install pyqtgraph
sudo pip install capstone
sudo apt -y install mtd-utils gzip bzip2 tar arj lhasa p7zip p7zip-full cabextract cramfsswap squashfs-tools sleuthkit default-jdk lzop srecord
cd binwalk
sudo python setup.py install
cd ..
sudo apt -y install zlib1g-dev liblzma-dev liblzo2-dev
cd sasquatch && sudo ./build.sh
cd ..
sudo pip install cstruct
cd jefferson && sudo python setup.py install
cd ..
sudo apt -y install liblzo2-dev python-lzo
cd ubi_reader && sudo python setup.py install
cd ..
cd yaffshiv && sudo python setup.py install
cd ..
sudo cp stuff/bin/unstuff /usr/local/bin/
|














